Verifying Signatures
By verifying the signatures of KeePassXC releases, you can prove the authenticity and integrity of the downloaded file. This guarantees that the file you just downloaded was originally created by the KeePassXC Team and that its contents haven't been tampered with on the way.
A more detailed explanation is available in the Qubes-OS project documentation.
Download Options
Every KeePassXC release is published in a variety of package formats:
- a
*.dmgdrag-and-drop installer for macOS - an
*.msiinstaller and a*.ziparchive with binaries for Windows - a self-contained executable
*.AppImagefor GNU/Linux. - a
*.tar.xzsource tarball
Each of these package files has two related sidecar files, a *.sig containing a PGP signature and
a *.DIGEST containing the SHA-256 hash for basic integrity checks.
Verifying Releases – Windows
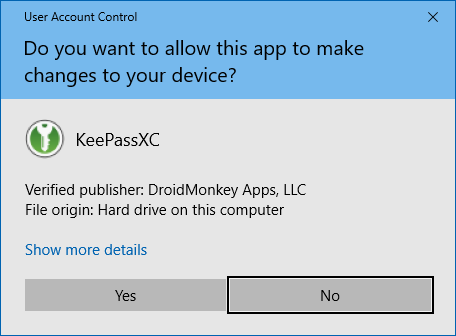
The Windows MSI installation file is protected by an authenticode signature, this means that authenticity and integrity checks are verified directly by Windows when you run the program.
You should see the following dialog with DroidMonkey Apps, LLC as the verified publisher:
To verify the portal ZIP file, you must download and install Gpg4win. Then follow the verification instructions below.
Verifying Releases – macOS
The macOS release is signed with our Apple Developer ID, which is checked by the operating system on launch. You won't be able to open KeePassXC after the installation if the signature check fails.
Verifying Releases via PGP – Linux, macOS, and Windows
A more thorough check can be made using the *.sig sidecar file.
This contains an OpenPGP (GPG) signature created with one of our release keys.
Signing files with any other key will give a different signature. Following these verification instructions will ensure the downloaded files really came from us.
Step 1: Import the public key
We will use the gpg program to check the signatures.
Before you can do that you need to tell gpg about our public key, by importing it.
On Windows and macOS you will need to install the gpg program. On Windows, we recommend
Gpg4win. On macOS we recommend
GPG Tools or gnupg installed via HomeBrew.
The KeePassXC public key can be retrieved with:
1$ gpg --keyserver keys.openpgp.org --recv-keys BF5A669F2272CF4324C1FDA8CFB4C2166397D0D2These are the fingerprints of the master key and the current signing sub keys:
1$ gpg --list-keys BF5A669F2272CF4324C1FDA8CFB4C2166397D0D2
2pub rsa4096 2017-01-03 [SC]
3 BF5A669F2272CF4324C1FDA8CFB4C2166397D0D2
4uid [ unknown] KeePassXC Release <[email protected]>
5sub rsa2048 2017-01-03 [S] [expires: 2024-12-04]
6 C1E4CBA3AD78D3AFD894F9E0B7A66F03B59076A8
7sub rsa2048 2017-01-03 [S] [expires: 2024-12-04]
8 71D4673D73C7F83C17DAE6A2D8538E98A26FD9C4Note that we have a master key and some sub keys. The actual signatures are created with one of the sub keys. As the naming implies, they are closely related to one another—importing the master PGP key is sufficient for verifying signatures made with any of its sub keys.
Step 2: Verify the PGP signature
Once you have imported the key, you can decide whether you want to mark it as trusted. This is not strictly necessary for the checks we are making here. For more information, see the Qubes-OS project documentation.
You can then verify the authenticity and integrity of a downloaded package from its detached signature by running the following command:
1$ gpg --verify KeePassXC-*.sigThe output should look like this (the file name will differ obviously):
1gpg: assuming signed data in 'KeePassXC-*'
2gpg: Signature made Thu 22 Oct 2020 01:57:33 CEST
3gpg: using RSA key C1E4CBA3AD78D3AFD894F9E0B7A66F03B59076A8
4gpg: Good signature from "KeePassXC Release <[email protected]>" [unknown]
5gpg: WARNING: This key is not certified with a trusted signature!
6gpg: There is no indication that the signature belongs to the owner.
7Primary key fingerprint: BF5A 669F 2272 CF43 24C1 FDA8 CFB4 C216 6397 D0D2
8 Subkey fingerprint: C1E4 CBA3 AD78 D3AF D894 F9E0 B7A6 6F03 B590 76A8You want to see that "Good signature" line. It shows that the .sig file must have been created from
the downloaded file with a PGP key with the primary fingerprint BF5A 669F 2272 CF43 24C1 FDA8 CFB4 C216 6397 D0D2.
In most cases, you should see the above result. But if the verification fails or the fingerprint does not match, do NOT install the package. First, try downloading it again. If the checks are still failing, let us know about the problem by opening an issue.
Basic Integrity Check
If you know what you are doing, can skip the authenticity check and perform only a simple integrity check of the file using the .DIGEST
sidecar file. This will ONLY tell you that the file has been downloaded correctly without errors. It will NOT tell you
if you can TRUST the download! If you have already followed any of the verification steps above, you do not need to do this.
Linux and macOS
Open a terminal window and change directory to the folder you downloaded the files to, e.g. cd /home/username/Downloads
The *.DIGEST file can be used to check your package downloaded correctly, with the following command:
1$ shasum -a 256 -c KeePassXC-*.DIGEST
2KeePassXC-*: OKThe shasum program recalculates the SHA-256 hash digest of the package file
and compares it with the value in the .DIGEST file. If they match (output is OK), the package was downloaded without errors.
Windows
Open a PowerShell window (hit WIN+R, type in powershell, press Enter) and change directory to the folder you downloaded the files to, e.g. cd C:\Users\username\Downloads
Copy/Paste the following command into the PowerShell window:
1(Get-FileHash .\KeePassXC-*-Win64.msi).Hash -eq (Get-Content .\KeePassXC-*-Win64.msi.DIGEST).split(" ")[0].ToUpper()You should see True appear. If not, then the download is invalid or your files are not together.